Incredibly Covert Malware Procedures - H@cktivityCon CTF
Category: Forensics
Solves (at time of writing): 140
Description: We got hacked! Can you see what they took?
Incredibly Covert Malware Procedures
We are given a pcap (network capture) file.
Opening it in wireshark yields us a few calls to spotify, and a whole lot of ping (icmp) packets.
Looking at the packets it looks like they have a PNG image embedded into them.
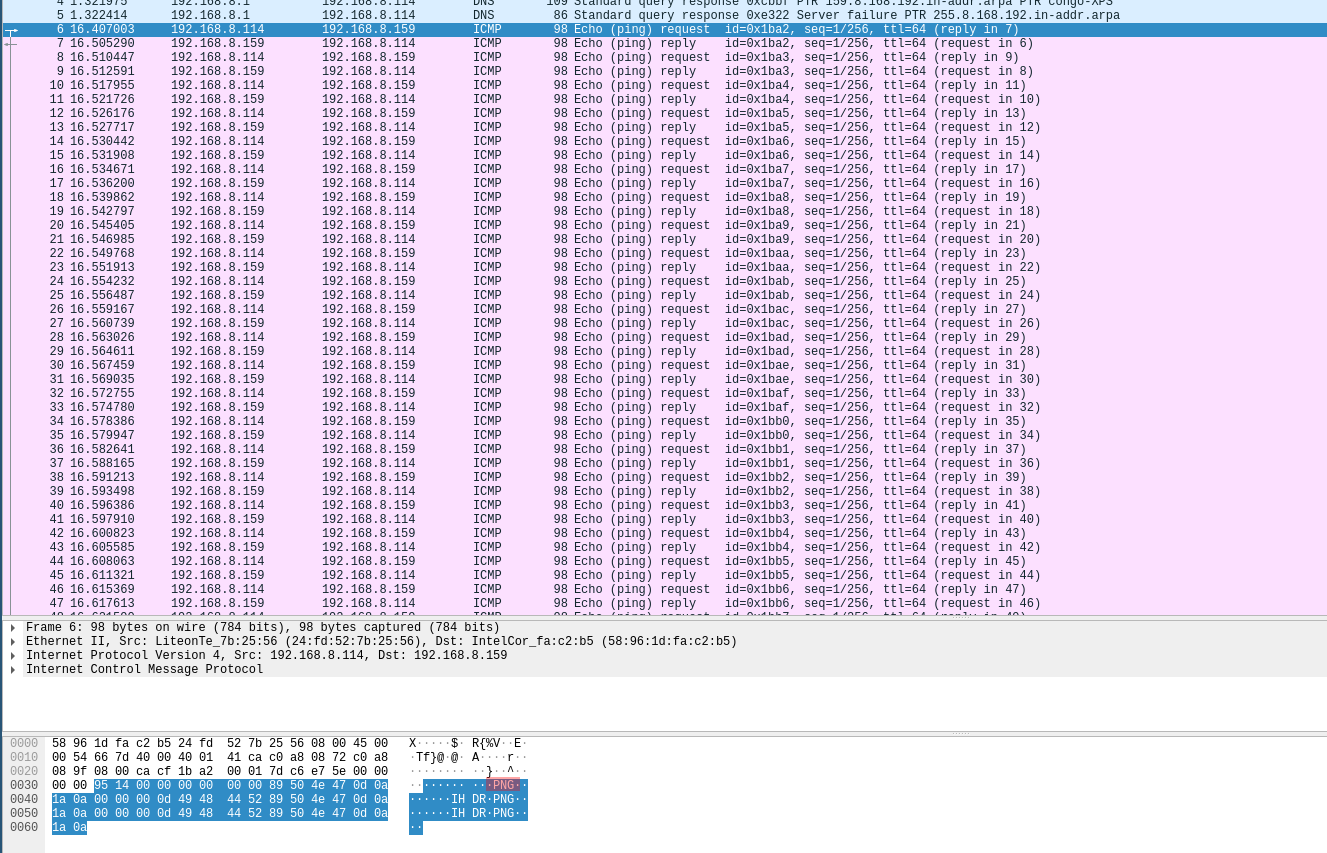
Here in red the PNG magic bytes.
Me not knowing enough wireshark returned to python, and I made a quick script that extracts the data from those requests.
Basically: Ignore the first few and last non-icmp packets, only get the relevant parts out of the packets, and only get data from every
2nd packet (odd numbers) since icmp "echoes" and we dont want those echoes inside of our png.
from pylibpcap.pcap import rpcap def isOdd(n): return n%2 i = 0 wholebuf = b'' for ln, t, pkt in rpcap("incident.pcap"): if i >= 5 and isOdd(i) and i <= 1431: wholebuf += pkt[58:74] i+=1 with open("test.png", "wb") as file: file.write(wholebuf)
Running this script on the pcap file yields us the flag as an PNG:
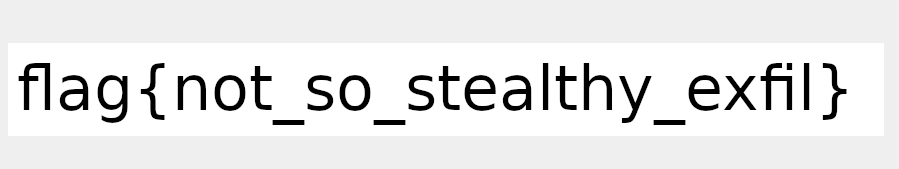
~sw1tchbl4d3, 03/08/2020 (dd/mm/yyyy)