Bite - H@cktivityCon CTF
Category: Web
Solves (at time of writing): 576
Description: Want to learn about binary units of information? Check out the "Bite of Knowledge" website!
Bite
We are presented with a small website.
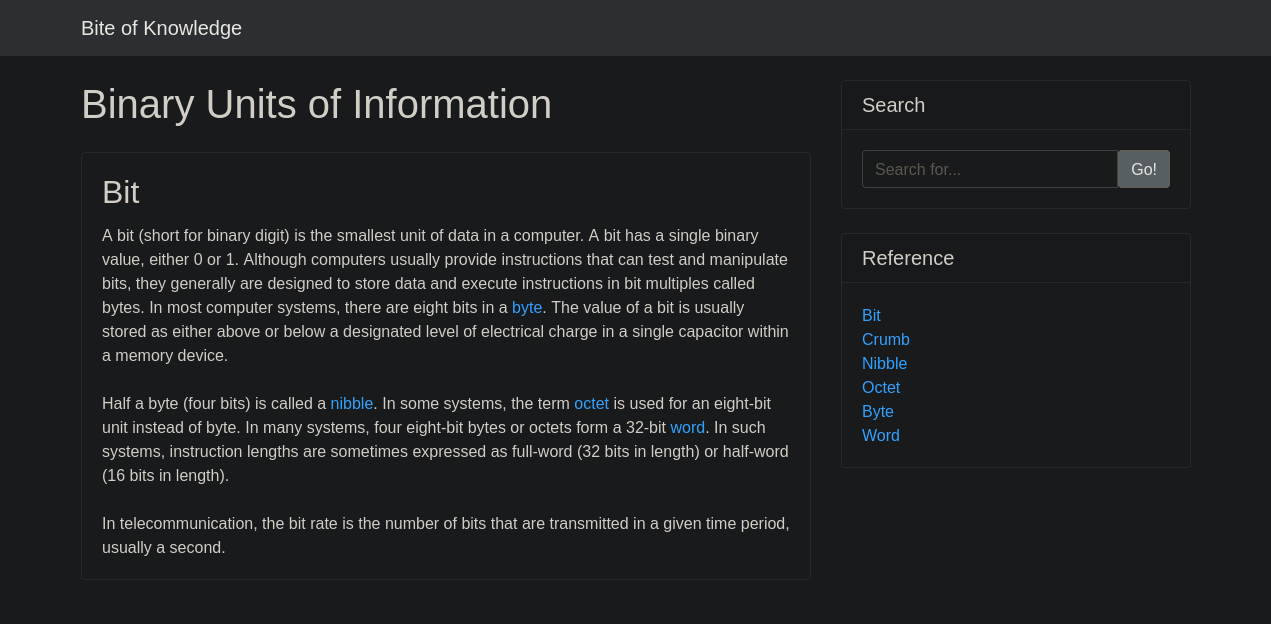
After a bit of clicking around on the reference links we quickly notice something.
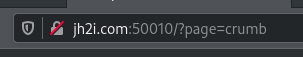
If I click on crumb, we get this in the url bar.
Here we see that the website determines what page to show with the ?page parameter.
This looks like a LFI (Local File Inclusion) vulnerability
We can test this by putting something invalid in this parameter, like ?page=doesntexist
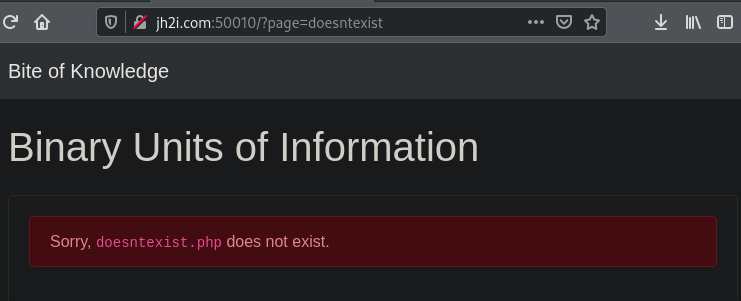
It tells us that doesntexist.php doesn't exist.
So yes, we can try to load files we're not supposed to see.
At first I tried the obvious flag, and that actually gave us a hint to where the file is located.
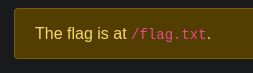
It tells us the flag is at /flag.txt
Trying that out (?page=/flag.txt) gives us the following:
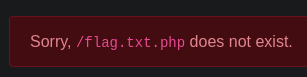
It appended a .php to the end!
But we can fix that by using a null-byte.
A null-byte basically just tells the computer that the string ends at some point.
In html parameters we enter a nullbyte by typing %00
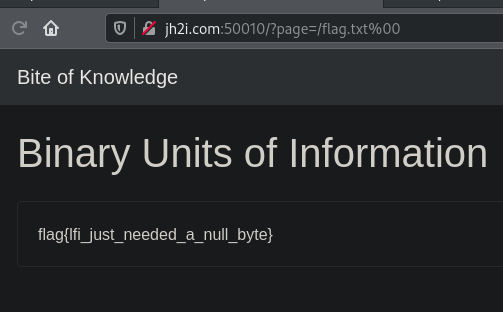
So the Website it'd look up isnt flag.txt.php anymore, but flag.txt%00.php
Since we have the null-byte, it cuts of the .php and we end with flag.txt
And we get the flag!
~sw1tchbl4d3, 31/07/2020 (dd/mm/yyyy)