Intro to Stegano 3 - CSCG
Category: Stego
Difficulty: Baby
Author: explo1t
Reconnaissance
This is the file we got:

(same file, unmodified! You can try it yourself!)
At first I tried to look at the image color-wise with this tool
(had to convert the png to jpg first though)
After my image was uploaded I tried every mode, and LSB Half got the result I needed.
Clicking that, the image got transformed into this:

As you can maybe see, it says The password is s33_m3_1f_y0u_c4n
We'll need that for our next step.
Running zsteg on the png got this:
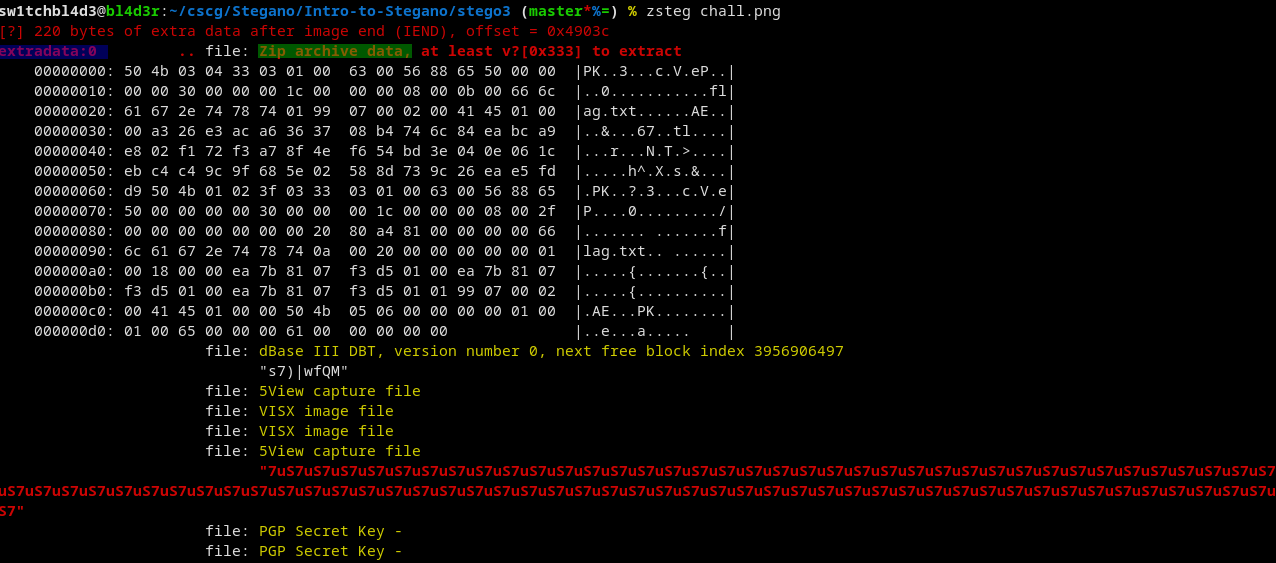
We found a zip file (green) at extradata:0 (blue).
Now to the "Exploitation".
Exploitation
We can extract the zip file from the png like so:
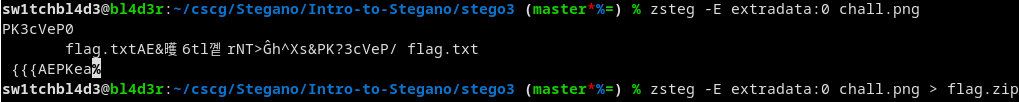
Trying to unzip the file asks for a password.
Conveniently we already know the password!
Extract the zip and cat out the flag and we get this:
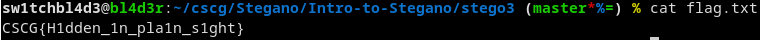
And there's the flag!
Mitigation
Like I said last time, stego isnt good if you haven't got a password that's not already contained in that/some other file.
Someone will eventually find it.
~sw1tchbl4d3, 09/04/2020 (dd/mm/yyyy)