Intro to Reversing 1 - CSCG
Category: Reverse Engineering
Difficulty: Baby
Author: 0x4d5a
Reconnaissance
Files for you to hack along: intro-rev1.zip
Starting the executable greeted me with the following:
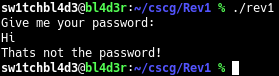
So we need to get the password.
As it is with reversing-challenges, I have my small checklist to go through.
At first I tried strings rev1.
Strings shows all strings inside of a binary, maybe theres something like the flag or the password in the file in plaintext.
To my surprise, the password was in the list of strings contained in that executable
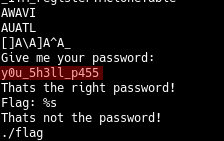
As marked here (in red), you can see y0u_5h3ll_p455 right after Give me your password: .
Exploitation
Thanks to our recon we now have the password to get the flag.
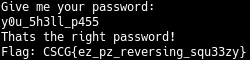
And there's the Flag! CSCG{ez_pz_reversing_squ33zy}
Mitigation
There are a few possible ways to stop getting in this way, but I'd recommend one that applies to Rev1-Rev3: Hashing.
Get a secure password, hash it with something secure like SHA-512, and save the hash in the file, not the plain password / poorly encrypted password.
Then hash the user input the same way, compare the hashes and nobody can read your passwords anymore!
~sw1tchbl4d3, 07/03/2020 (dd/mm/yyyy)