Intro to Crypto 2 - CSCG
Category: Crypto
Difficulty: Baby
Author: black-simon
Reconnaissance
Files for you to hack along: intro-crypto2.zip
I looked at the Modulus and the Exponent at first, both look reasonable.
Trying to factor the Modulus again didn't work, so I got me some help from a cool tool.
Exploitation
To get the private key I used RsaCtfTool.
Issuing ./RsaCtfTool.py --publickey ../pubkey.pem --private yields us this:
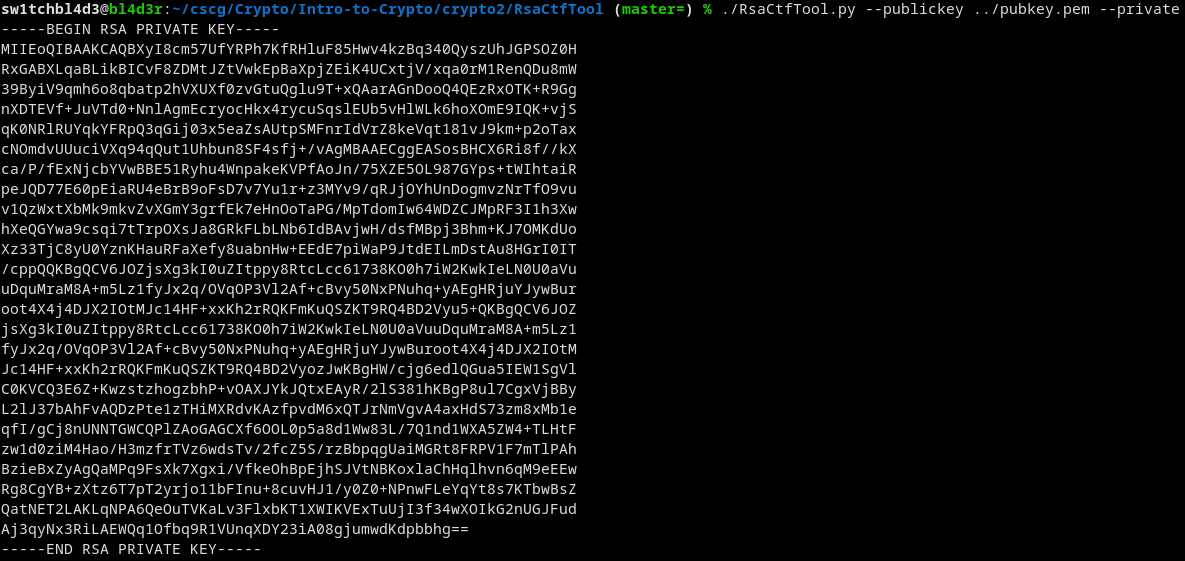
That wasn't too hard.
Now we can extract the private exponent from this key by executing cat privkey.pem | openssl rsa -text -noout.
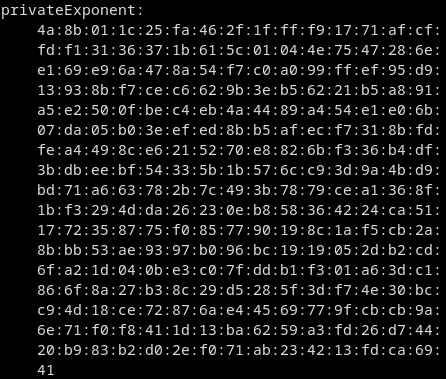
This is our d.
Converting this into a number with my modtodec script gets us this:
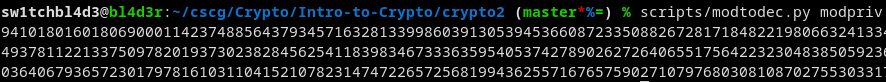
Too large to show here once again.
Knowing D we can decrypt the message like we did in Intro to Crypto 1.
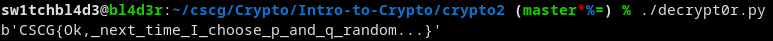
Mitigation
First of all: Don't generate your own custom keys with custom primes like this. Use tools that have been tested like openssl etc...
And if you want to generate them manually, check the security of the two primes and the private and public exponent.
~sw1tchbl4d3, 09/04/2020 (dd/mm/yyyy)